Hi,
Today, I want to go through the process of finding a physical device in a network if you only have an IP address or a MAC address. This is my way of doing it, and it is very simple actually. Of course there could be a better way of doing it, I don’t know of.
For this example, I will be using Netgear and Aruba Switches, both of which we have in the office.
The process is, like I said, very simple, but our trainees tend to forget about it. We will be using the ARP table on the switches to pinpoint the exact port on which the device is.
Here is a simplified topology of the network. My goal is to find the “webterm-1” client. The MAC we have is the “a0:36:9f:5b:23:bb”
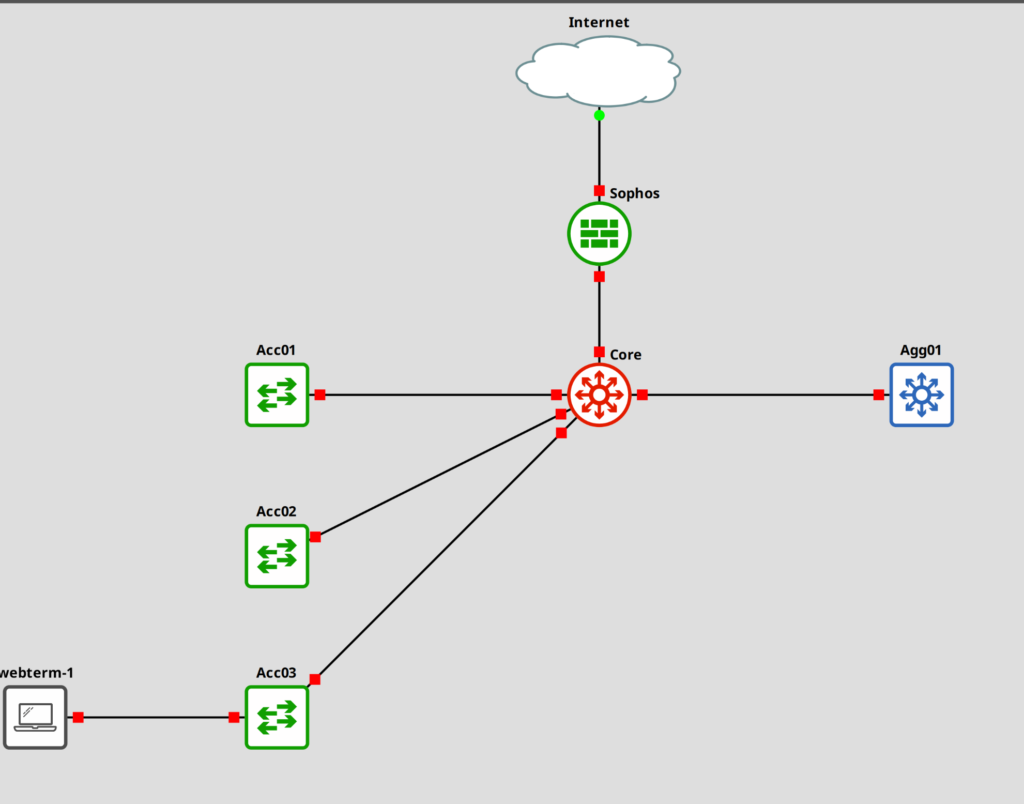
Let’s begin.
Using the ARP Table
This method assumes that at least one switch has registered the MAC address of that device. If not, it won’t show up in the address table. Also, this works in a flat (Layer 2) network. If you have a routed network, then, if you have the IP, you could use “tracert” on Windows or “mtr”/”tracepath”/”traceroute” on Linux to get the last hop and go from there.
The most logical point, to start, would be the core switch. Since it’s centralized, it allows us to quickly reduce the potential switches, the device could be connected to. We use Aruba Switches for our “core”, most of the access switches are Netgear. We will replace those in time, but this allows me to show the different CLI’s.
First, we log into the Aruba switch. This will be an Aruba 2930F. The output will be slightly modified for privacy reasons.
# List ARP table core# show arp IP ARP table IP Address MAC Address Type Port --------------- ----------------- ------- ---- 172.16.0.20 000056-000000 dynamic 49 172.16.0.151 a0369f-5b23bb dynamic 49 172.16.0.217 005006-000007 dynamic 49 172.16.0.254 001a8c-4c0008 dynamic 49
We could also filter the search like this.
core# show arp | include 23bb 172.16.0.151 a0369f-5b23bb dynamic 49
Ok, we have our device. As we can see, it’s on port 49, but since there are multiple devices on that port, we can assume that we have another switch on that port. Let’s check LLDP.
core# show lldp info remote-device LLDP Remote Devices Information LocalPort | ChassisId PortId PortDescr SysName --------- + ------------------ ------------------ --------- ------------------ 25 | f44d30-000000 f4 00 30 00 00 c7 47 | 000000-c2c06c fc 7f 00 c2 00 6c eth0 Besprechungszim... 49 | 53L69C5CF0036 3/0/51 M4300-52G-PoE+
Yes, it is another switch. One of the Netgear M4300 to be precise. We can get the IP address of that switch using LLDP. Not every device publishes the IP, but I know that the Netgear switches do.
core# show lldp info remote-device 49
Local Port : 49
ChassisType : mac-address
ChassisId : 000000-000000
PortType : local
PortId : 3/0/51
SysName :
System Descr : M4300-52G-PoE+ ProSAFE 48-port 1G PoE+ and 2-port 10GBASE...
PortDescr :
Pvid :
System Capabilities Supported : bridge, router
System Capabilities Enabled : bridge, router
Remote Management Address
Type : ipv4
Address : 172.16.0.220
Great. Let’s log into this switch.
Once logged in, we need to change into the “user privilege mode”. Here we can show the ARP table.
# Change into the "user privilege mode" (M4300) > enable (M4300) # show arp Age Time (seconds)............................. 1200 Response Time (seconds)........................ 1 Retries........................................ 4 Cache Size..................................... 760 Dynamic Renew Mode ............................ Enable Total Entry Count Current / Peak .............. 44 / 91 Static Entry Count Configured / Active / Max .. 0 / 0 / 128 IP Address MAC Address Interface Type Age --------------- ----------------- -------------- -------- ----------- 172.16.0.20 00:50:56:00:00:00 vlan 1 Dynamic 0h 0m 13s 172.16.0.44 00:50:56:00:00:01 vlan 1 Dynamic 0h 2m 33s 172.16.0.55 00:00:56:00:00:02 vlan 1 Dynamic 0h 12m 15s 172.16.0.65 24:5E:00:00:00:C1 vlan 1 Dynamic 0h 0m 49s 172.16.0.66 24:5E:00:2C:00:BF vlan 1 Dynamic 0h 10m 13s 172.16.0.181 9C:5A:00:00:ED:6C vlan 1 Dynamic 0h 0m 54s 172.16.0.209 00:50:56:9E:F3:65 vlan 1 Dynamic 0h 6m 14s ....
Searching through over 200 addresses isn’t fun, so let’s filter it.
(M4300) # show arp | include 23:BB 172.16.0.151 A0:36:9F:5B:23:BB vlan 1 Dynamic 0h 0m 8s
Ok, the switch knows about the device, and we know it’s in VLAN 1. But it does not tell me the interface. I couldn’t find a way to show the port on which the MAC was, through the CLI, so let’s check the web UI.
Navigate to “Switching” -> “Address Table” and search for the mac address.
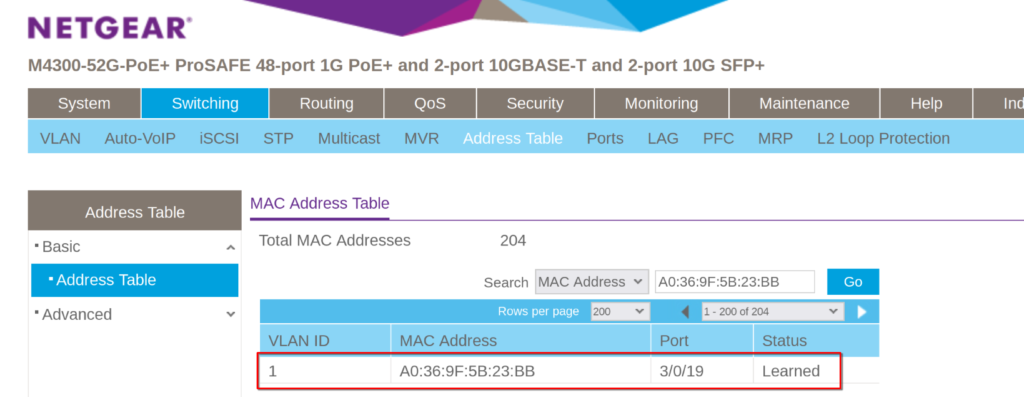
Alright, we have a port. Let’s search for the port, just to verify if there are more devices on that port.
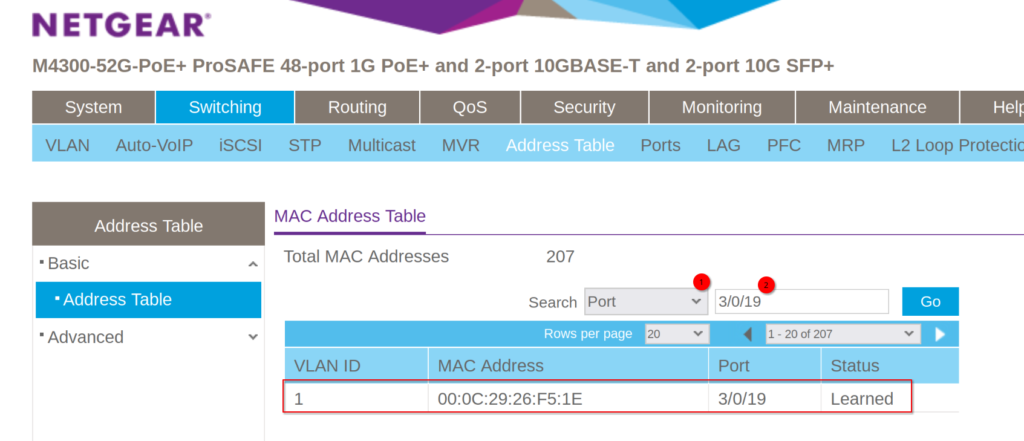
Seems like we have our device now. Let us take a look at the LLDP information.
Alright, I am going to blur most of the information. It basically does not show up in the table. Which means we probably have our device.
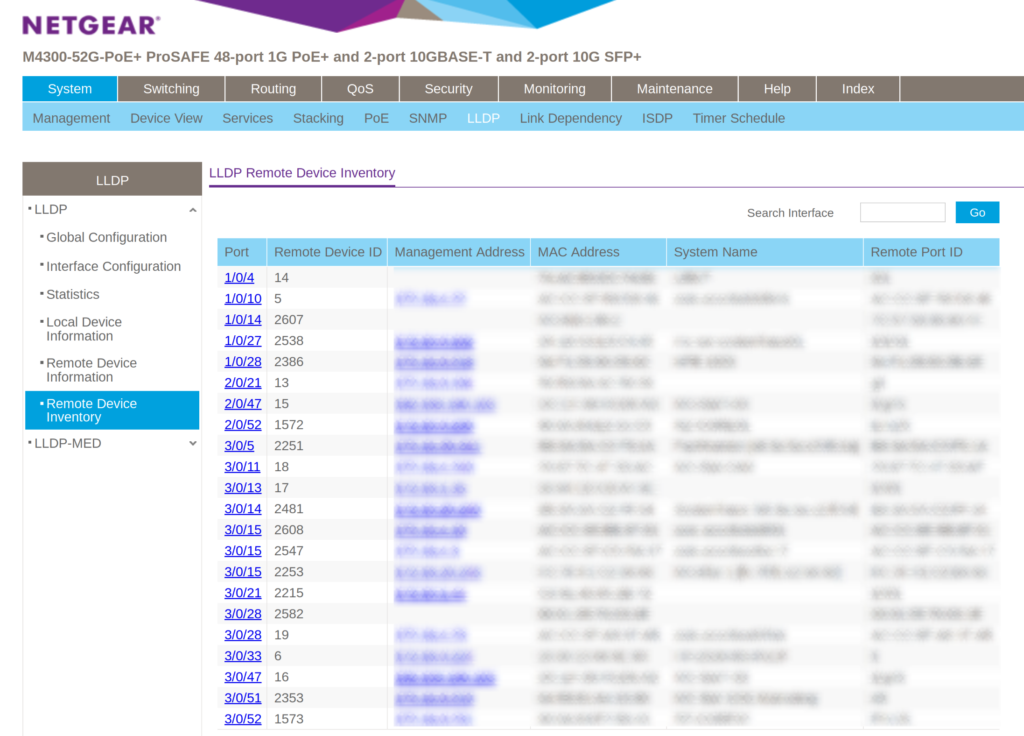
The only thing left, would be to physically follow the cable to the device.
What if I only have an IP Address?
If you actually have an IP address than it becomes a lot easier. In case the switches do not have the MAC address in their table, you can just ping the device. This actually also works in case the system does not answer the ping request.
After pinging, the ARP table should be populated with the IP and MAC of the device. After that, you can just follow the steps above.
Bonus: Find Sophos Interface
This comes actually quite handy in finding which port a Sophos Firewall is attached to. Because for whatever reason they did not implement LLDP.
So, if you have access to the Sophos Web UI, then grab the MAC address of the interface you want, log into the directly attached switch and do a “show arp”. Or just ping the Gateway IP which will populate the table.
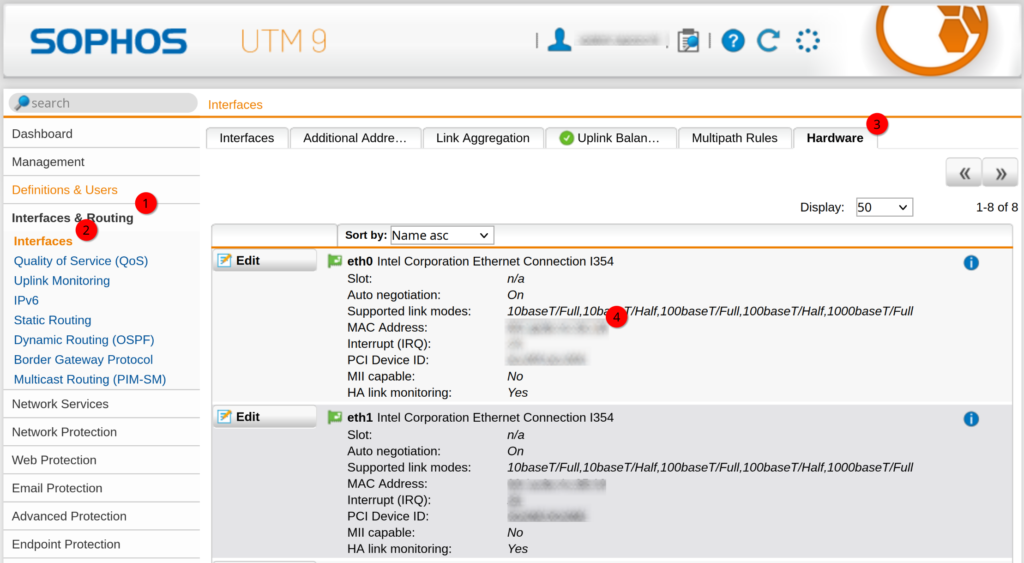
On a Sophos SG, you can get the MAC addresses through the “Hardware” tab.
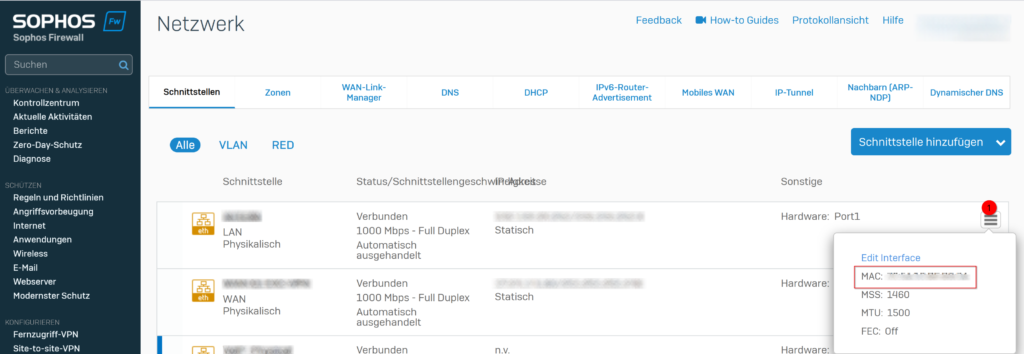
On the Sophos XGS / Sophos Firewall, navigate to network and click on the hamburger menu on the right of the interface.
Alright. That’s it for today.
Hope this helps someone. Till next time.