Hi there,
today will be a short one… I think.
I want to show you, how to set up the SSO with OpenID in MinIO using Authentik. In this, I am not going to show how to deploy the applications (I already did with MinIO). So I am assuming you already have a running Authentik and MinIO server.
Let’s begin.
Authentik Configuration
Create a Property Mapping
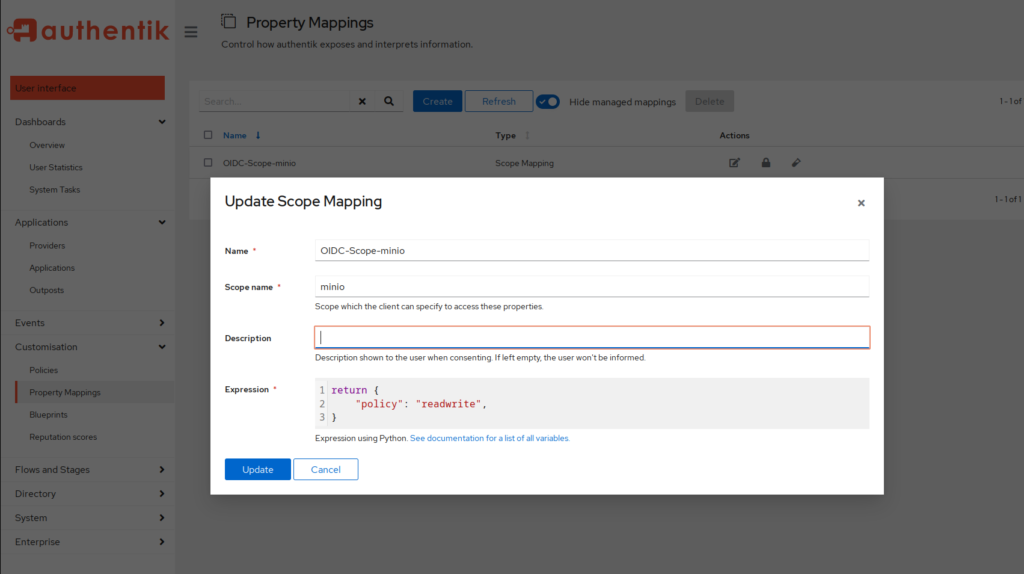
First, we will set up a role mapping. Login to Authentik and switch to “Customisation” -> “Property Mappings” and create a new one.
In here, give it a scope name and enter the following under “Expression”. You can get more details on the official documentation for Authentik.
return {
"policy": "readwrite",
}
Create Provider
Now we need the to create an Application and Provider for MinIO.
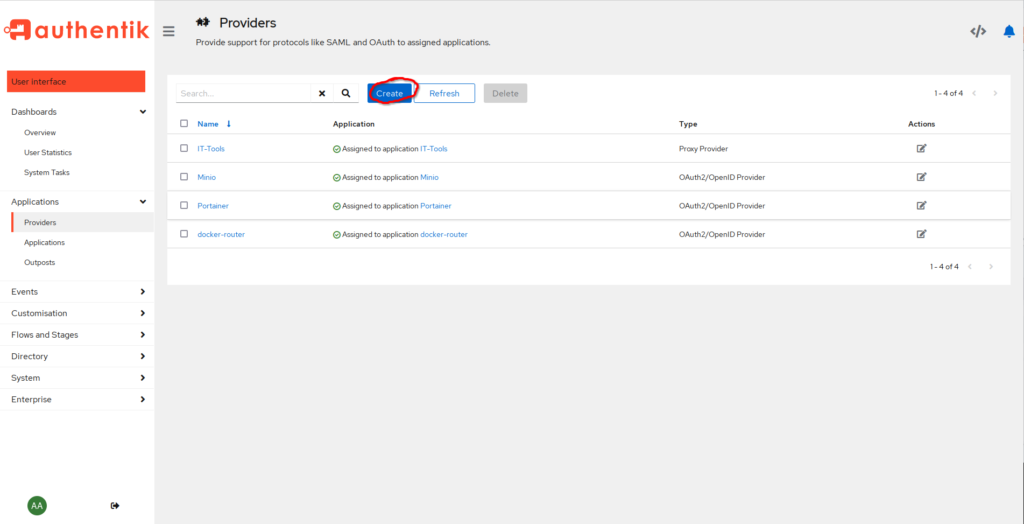
Let’s begin with the “Providers”. Navigate to “Applications” -> “Providers” and click on “Create”.
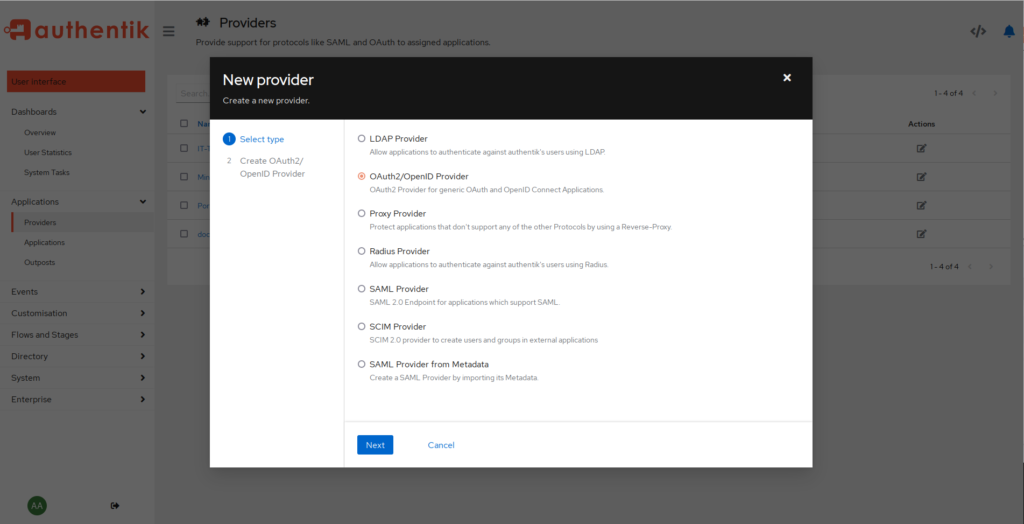
Choose the type. In our case, the OAuth2/OpenID provider.
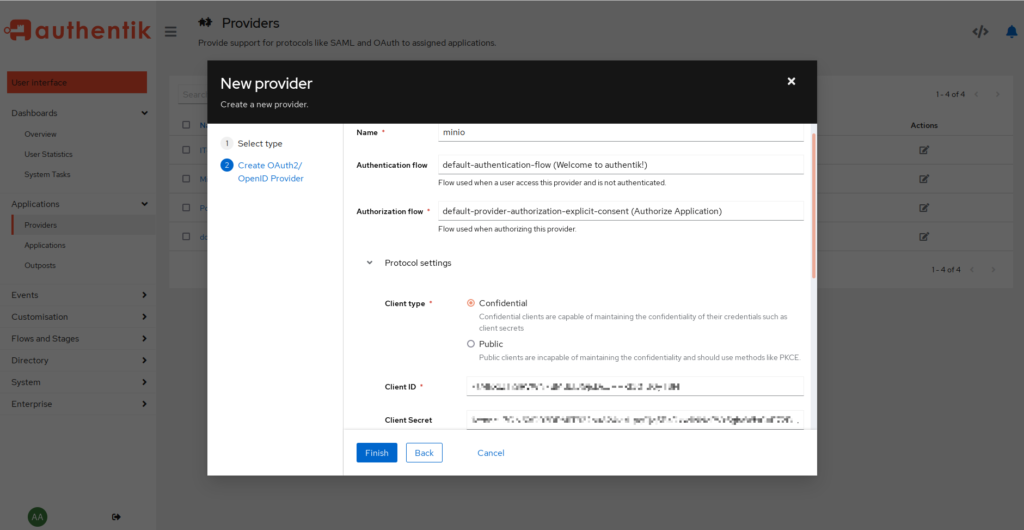
Next, give the provider a fitting name. I will just use minio and take note of the “ClientID” and “Client Secret”. In the “Authentication flow” and “Authorization flow”, you can choose the defaults.
After that, click on “Finish”.
We should have a new entry with an error message telling us that we need to assign an application to this provider. We will do that next.
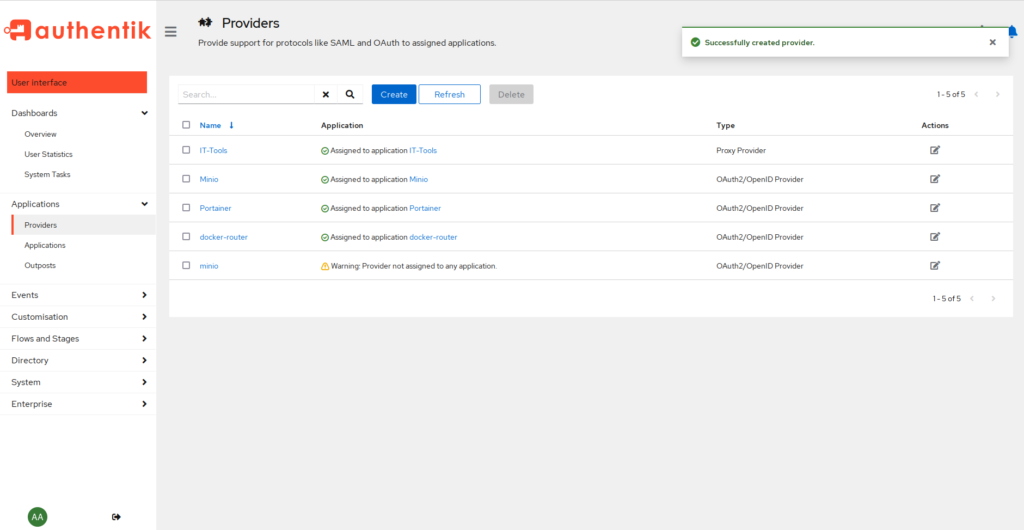
Create Application
Alright. Let’s continue. Switch to the “Applications” tab below providers, and click on “Create”.
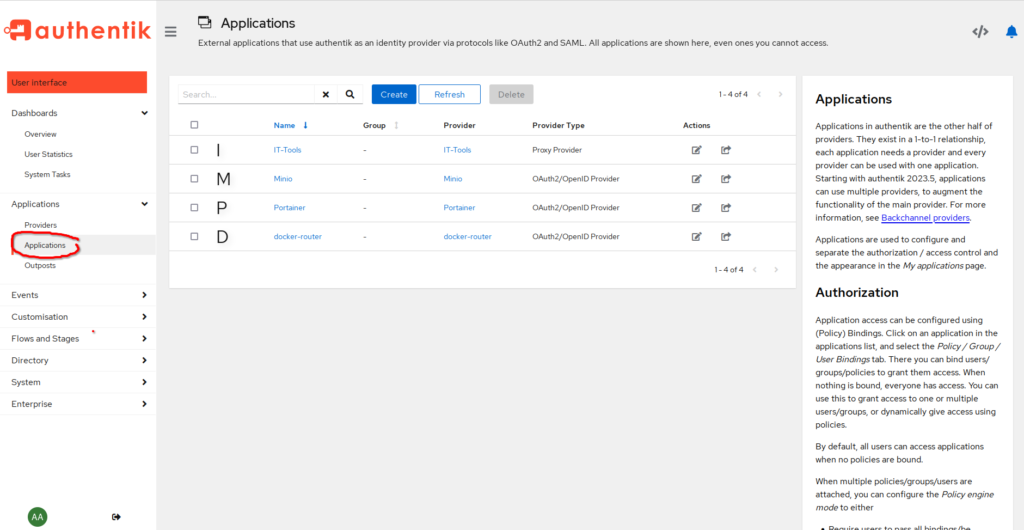
Again, enter a fitting name. I will use the same for the “Slug”, and choose the provider we created earlier. You can enter the URL for MinIO in “Launch URL” but it should also work without that entry.
Click on “Create” and that’s it.
OK. Switch back to the “Providers” and click on the newly created “minio” object. We get a bunch of URLs. Take note of the first one “OpenID Configuration URL”
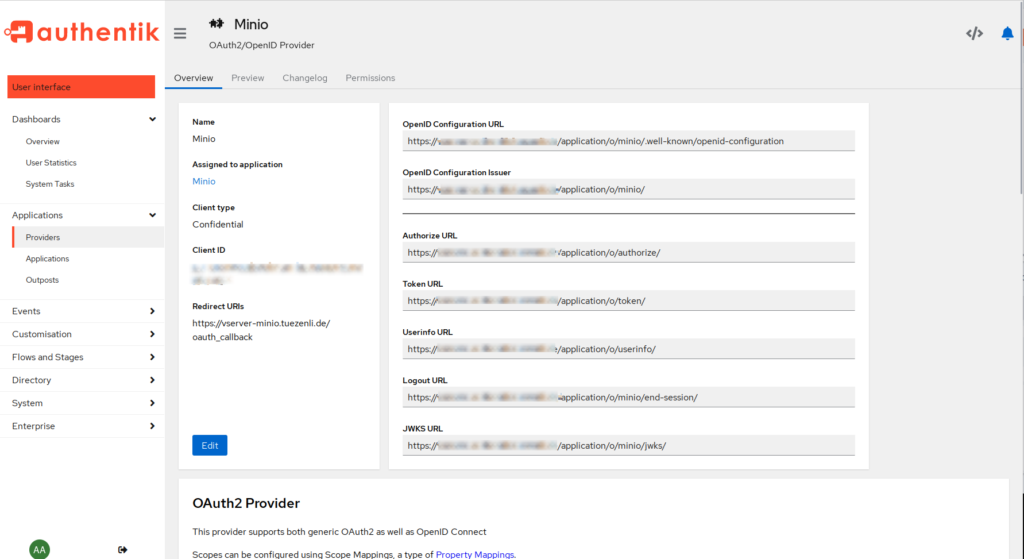
MinIO OpenID Configuration
Great. Lets setup Minio.
Once logged in, switch to “Identity” -> “OpenID” and click on “Create Configuration”.
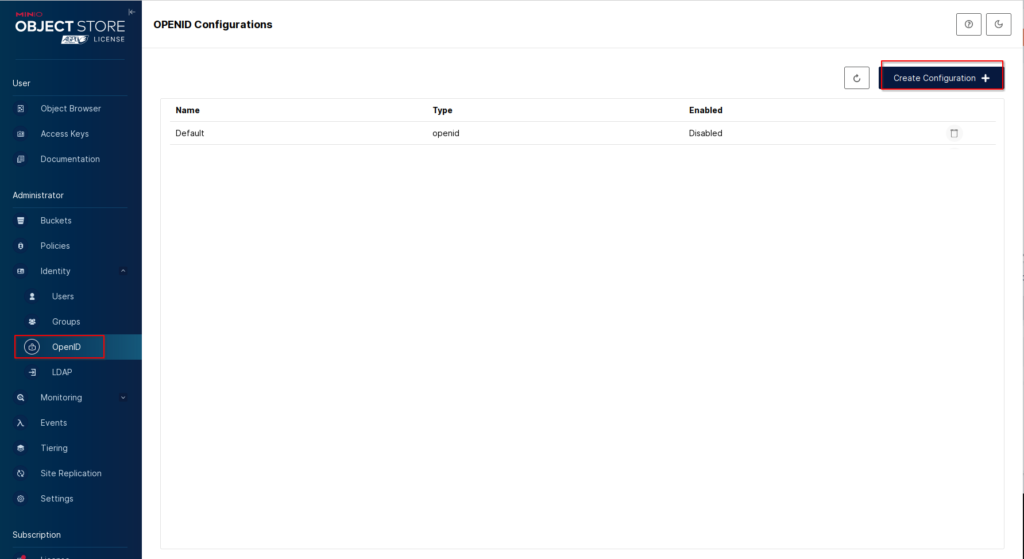
Here we give it a name, I will use “Authentik”, enter the URL we copied earlier and enter the Client ID / Client Secret.
For the “Scopes” enter the following “openid,profile,email,minio” and “https://minio-server-url/oauth_callback” for the “Redirect URI”.
Keep in mind that the “Scopes” entry depends on the first configuration we did. So if you used a different name for the “Role Mapping” you have to adjust the name here.
The “Role Policy” defines the permissions the users authenticating through OpenID have. Default is “readonly” but I will use the “consoleAdmin”.
Save the setting, and that should be it. At this point, you should be able to authenticate using Authentik credentials.
New MinIO login
Let’s log out and see what it looks like.
We should see a new button. “Login with SSO (Authentik)”.
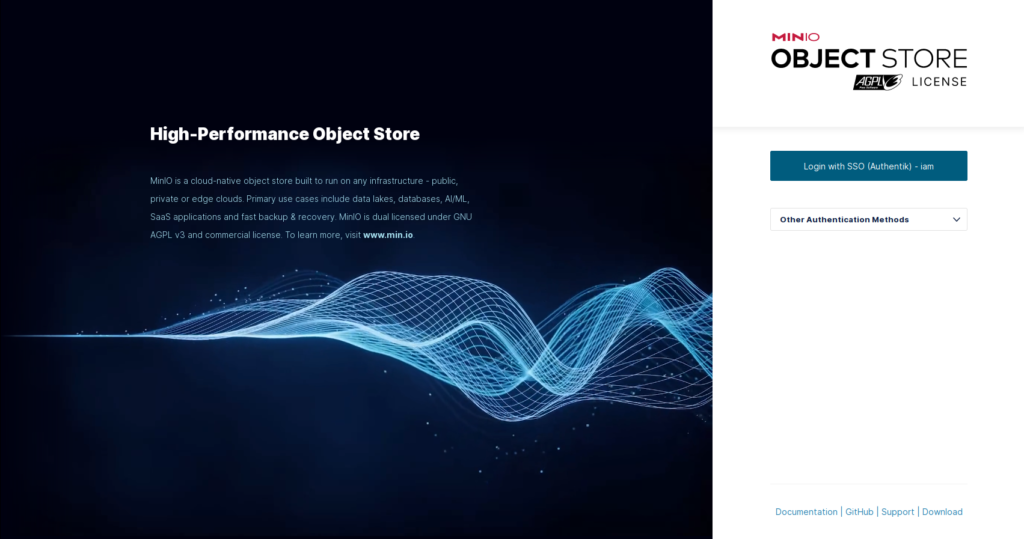
That’s it. Hope this helps.
Till next time.
Coooooool !