Hi there.
there are a few options to track traffic in Sophos, but none are as in-depth as tcpdump (as far as I am aware at least). The problem here is, that it is not as intuitive to capture the packages, copy the pcap file locally on your PC, and then open it with Wireshark.
What if there would be a way, to live capture the packages directly over SSH and pipe them into Wireshark… well there is (otherwise this would be a very pointless post) and I will show you how it’s done. I am using Fedora for this as usual, but this should work with most Linux distributions.
Let’s begin.
Preparation
First let’s create the ssh keys. I will use the ed25519 type of key since it’s faster and more secure than the default RSA.
fedora-kde :: ~ » cd ~/.ssh fedora-kde :: ~/.ssh » ssh-keygen -t ed25519 -C SOPHOS-LOGIN Generating public/private ed25519 key pair. // You can change the filename and path here. Enter file in which to save the key (/home/user/.ssh/id_ed25519): sophos-login // Here you can either enter a password or leave it blank. Enter passphrase (empty for no passphrase): Enter same passphrase again:
It should have generated 2 files “sophos-login” and “sophos-login.pub”. The first one is your private key. Handle this file as if it’s your login password, especially if you leave the password blank. Meaning, keep it safe.
The second one is your public key. This one is not as critical and can easily be recreated, in case it’s lost.
fedora-kde :: ~ » ssh-keygen -y -f ~/.ssh/sophos-login > ~/.ssh/sophos-login.pub
We will import the public key into Sophos. Display the content of the file and copy everything. We will need it later.
fedora-kde :: ~/.ssh » cat sophos-login.pub ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIFNkFxDSTxtqZitcYKj1kbc87ccfio03OvRghxgpemEE SOPHOS-LOGIN
Now that we have the keys, we can configure the Sophos Firewall.
Sophos SG configuration
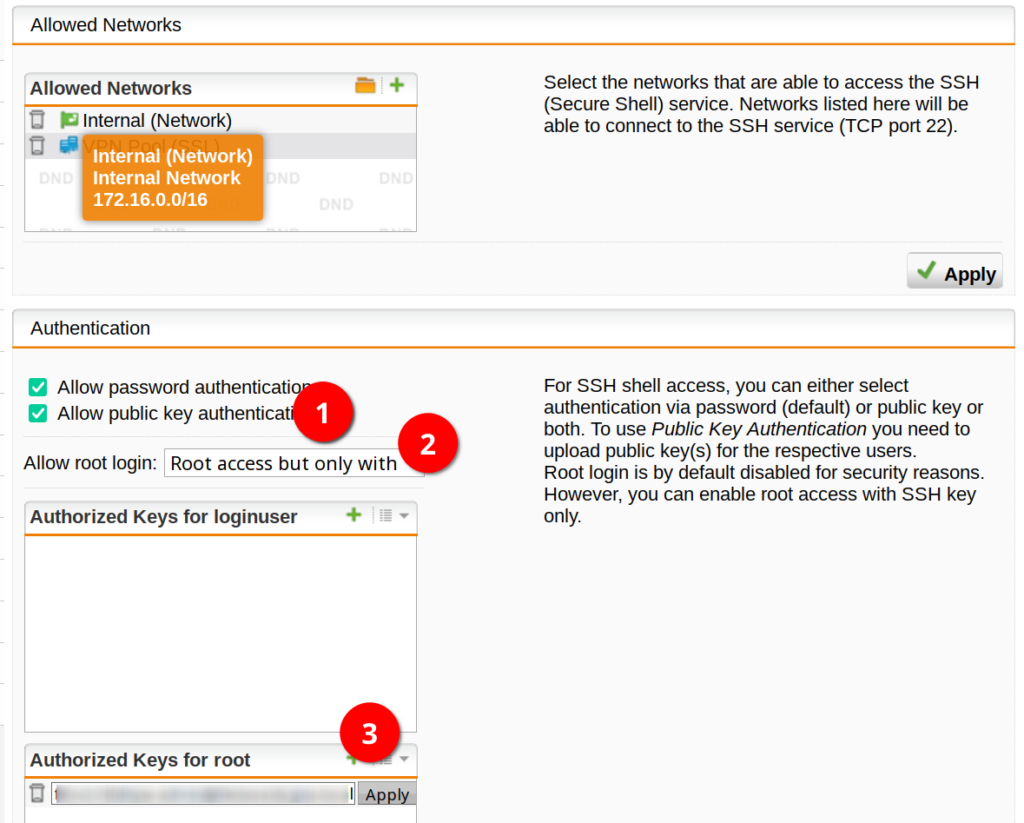
First, we need to enable SSH access to the Sophos SG. For this, we need to go to “System Settings” -> “Shell Access”.
Here we can enable SSH, enter a password for the “root” and “loginuser”, configure the allowed networks and add public keys for the users.
Enable SSH with the button on the right (3).

Add the networks to the “Allowed Networks” you want to access your firewall from.
Enable “public key authentication” (1) and “Root access but only with SSH key” (2).
Click on the Plus button in the “Authorized Keys for root” segment (3) to add a new public key and paste you public key you copied earlier. Make sure to apply the key and the configuration.
Wireshark remote connection over SSH
Ok, now we should be able to pipe the output into Wireshark over SSH.
fedora-kde :: ~ » ssh root@172.16.16.254 -i ~/.ssh/sophos-login "tcpdump -i eth0 -w -" | wireshark -k -i -
This will start Wireshark and start the capture on the interface “eth0”.
You could also limit the tcpdump capture to specific ports or protocols. For instance, if you only want to see UDP traffic on port 123.
fedora-kde :: ~ » ssh root@172.16.16.254 -i ~/.ssh/sophos-login "tcpdump -i eth0 udp port 123 -w -" | wireshark -k -i -
But this kind of defeats the purpose of remotely opening it with Wireshark, since you could also just filter it within Wireshark.
(Optional) Add Host entry for easier connection
You can add an entry to the ~/.ssh/config file with the ssh parameters. This is quite useful especially if you connect to the same device often.
fedora-kde :: ~ » vim ~/.ssh/config Host sophos hostname 172.16.16.254 User root IdentityFile ~/.ssh/sophos-login
Now you only have to type “ssh sophos” if you want to connect to the firewall.
fedora-kde :: ~ » ssh sophos "tcpdump -i eth0 -w -" | wireshark -k -i -
That’s it. Till next time.