Hey there.
Today I want to tell you about a small issue a colleague of mine encountered with a customer. This is not a large business but the customer works as a contractor, for one of the largest companies in the automobile industry. And there are a lot of hoops you need to jump through, to be allowed to work for this company, which I will call “big company” from here on.
One of these is the required level of security of the network our customer needs. Keep in mind that our customer is tiny. Around 10 users.
Here is only a rough topology of the network, since I did not build it (the colleague did. I was just asked to help out, because of the mentioned issue).

As you can see, not really complex. The main problems come from the fact, that getting any information from “big company” on how they configured the devices wasn’t easy. So what firewall rules, IP addresses and so on.
The hardware we configured are the “Internal Firewall”, “RED”, “Internal Switch” and what I will call “Transit Switch”. I don’t know why we have that switch, it was a requirement.
We have a separate network between the Internal and external firewall. On the internal firewall, we simply created a static route that forwards the required traffic to the external firewall.
Anyway, after a lot of back and forth, we finally had a running configuration.
The problems start in the home office scenario. The customer lives quite far away from the office, so wants to work from home whenever possible. All he needed was access from “PC1” (1) to “Important_Server” (2). So my colleague deployed a Sophos RED for the customer to take home.
But, as you might have guessed, it did not work. Internet and access to the internal servers worked, but no access to “big company”. The reason is quite simple. Even if we route the traffic to “Big company”, they won’t allow some random network to access their systems (and of course the missing route back on their side). Also, they need to keep track of the networks their contractors and branch offices use.
We tried a few things. First I wanted to see if a simple SSL VPN on my client would work, if I NAT the traffic into “big companies” network. So basically tell the “external firewall” that my IP is that of the “internal firewall”.
This worked quite nicely, which tells me that “big company” did not implement some kind of filter. Like a simple MAC address filtering for instance.
So, why not just NAT the traffic that comes from the RED device? I really expected this to work, but for whatever reason, no data went through. I don’t know where in the configuration I made a mistake.
Next plan. Bridging the RED to the internal network. Admittedly I only knew about it but never actually had a use case for this, so never implemented it before.
And that is why we have this post…
The configuration is quite simple. I will skip the RED setup for multiple reasons. Mainly because I don’t have one at hand right now. :).
Configure Interface Bridge
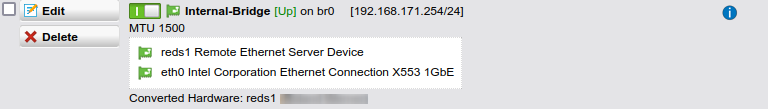
Once you setup your RED device (either using the assistant or manually), there will be a new interface added to the Sophos.

Setup new interface
Go to “Interfaces & Routing” -> “Interfaces” and click on “New Interface”.

Click on the drop-down menu “Type:” and select “Ethernet Bridge”. Select the new RED device (usually called reds1) and the interface you want to bridge it with. Set your IP for the bridged network and save the configuration.

If you want to bridge to an existing network, then edit that interface and change the type to “Ethernet Bridge”. You should be able to choose the new reds1 interface.
Configure the firewall
Next, we need to configure a firewall rule to allow DHCP traffic between the DHCP Server and the devices behind the RED.
Go to “Network Protection” -> “Firewall” and create a new rule.
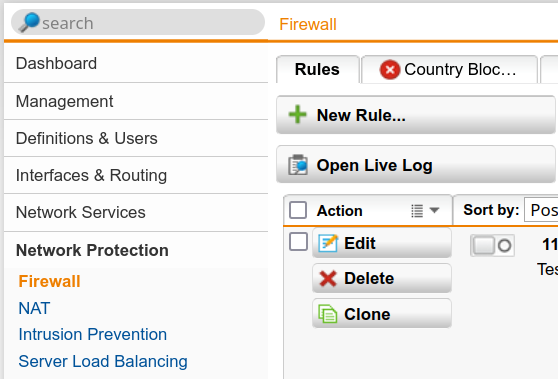
In this rule, we will define the bridge network as the source and destination. For the service we choose DHCP.

Setup Masquerading/NAT
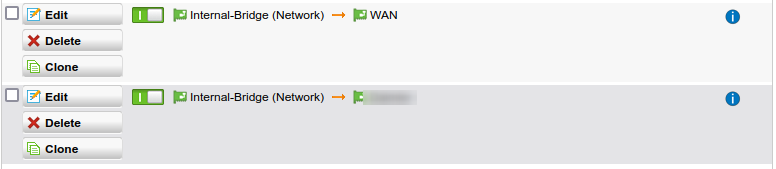
The last step is to configure the NATting. Go to “Network Protection” -> “NAT” -> “Masquerading”. and create a new masquerading rule. Set the “Network:” to the new bridge network and the interface to “WAN” (or whatever you called your Internet interface).
We also created another rule for the “big company” network. Didn’t test it without that but I think it should work since it’s the same network. Setting the NAT just seemed simpler in this case.
That’s it.